Threat Alert
Security Warning: Don’t Talk to Strangers on Facebook
A report by Avast’s Threat Labs has identified a new strain of spyware being distributed via a fake Kik Messenger app, luring users through falsified Facebook profiles. Callum Tyndall investigates the threat
Avast’s Threat Labs has put out an early threat identification warning about a new strain of spyware, dubbed Tempting Cedar.
Posing as the Kik Messenger app, the spyware, also known as an advanced persistent threat, is designed to steal personal information such as contacts, call logs, SMS and photos.
Perhaps more concerning, it is also capable of taking device information, including geolocation and recording surrounding sounds, such as any conversations the victims may have around the infected device
More than just friends: Faking Facebook
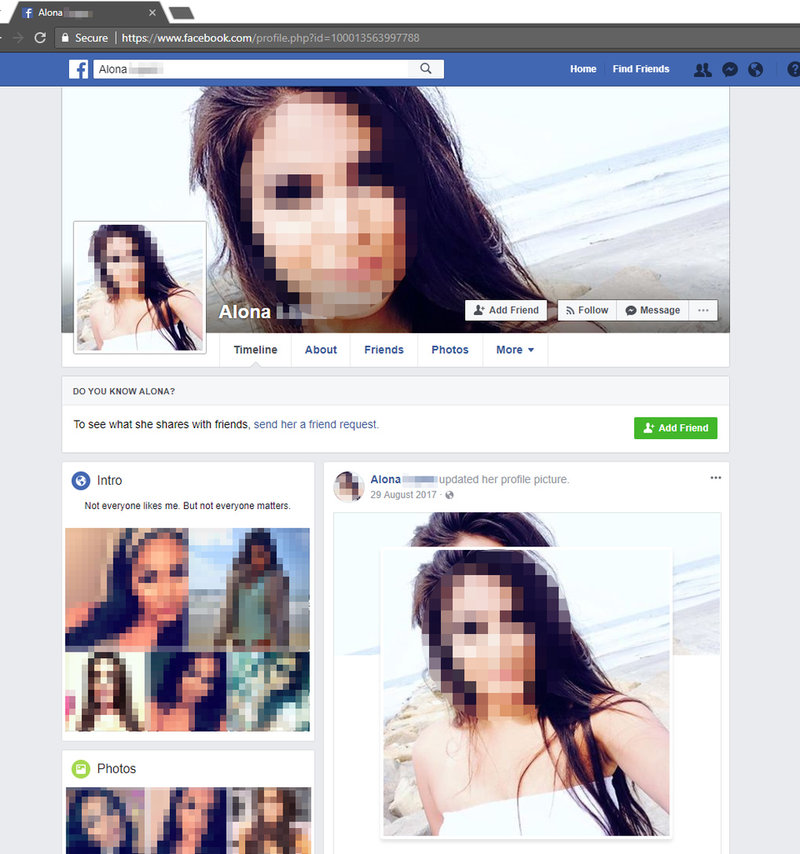
Avast first became alerted to the threat after a customer asked it to look into messages he’d been receiving on Facebook Messenger from people he didn’t know. Notably, the Facebook profiles were all those of attractive women, encouraging the customer to continue their conversations on Kik.
These profiles, which inevitably turned out to be fake, would encourage victims to visit a remarkably convincing site that they could download the Kik Messenger from.
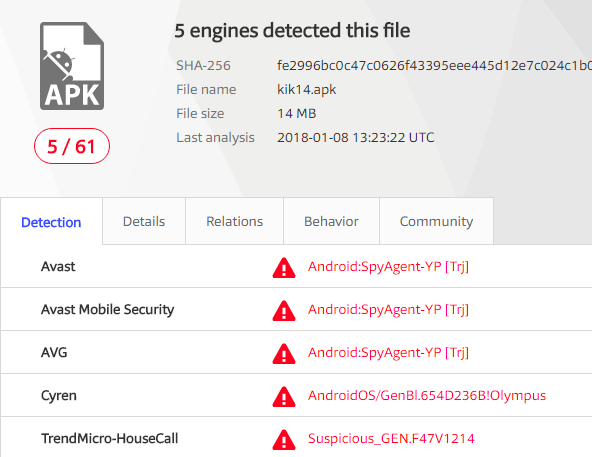
The doppelganger app they received would then go about stealing the desired information via a series of malicious modules that Avast has since found to have been contained within several fake messenger and feed reader apps.
At least three false Facebook profiles were used to spread the spyware ,and followed the same pattern each time: engage a victim, likely a young man, in flirty conversation, direct them to a more ‘secure and private’ platform (the phishing website hosting the infected app), then have them adjust their device settings to install apps from unknown sources and finally install the app itself.
The three profiles would even interact with each to appear more realistic, and the phishing website (which operated until spring 2017) was a surprisingly convincing copycat.
Command & Control: A persistent spyware service
Once installed, Tempting Cedar immediately connected to a command & control (C&C) server that allowed the attackers to live track their victims.
According to Avast’s report, among the spyware’s modules, “there are several modules designed to gather personal information about the victim, including contacts, photos, call logs, SMS, as well as information about the mobile device, such as geolocation, Android version, device model, network operator and phone numbers.”
The spyware would even run after every reboot, persisting as a service.
Contained within the application were the injected malicious class eighty9.guru and a specific rsdroid.crt file with different certificates belonging to the C&C domain.
By following the reuse of the rsdroid.crt certificate, Avast was able to find additional C&C and data exfiltration servers. Moreover, the analysis was able to identify the region where Tempting Cedar was spreading the most.
Linked to Lebanon: Tracing the attackers’ likely origin
The Avast report is open about the fact that the lab cannot guarantee the location of the attackers, noting that, “it is always difficult to attribute persistent threat campaigns, like this one, to cybercriminals”.
However, the clues it did manage to turn up strongly indicate the likelihood of the attack originating from a Lebanese hacker group.
In addition to the majority of the victims being located within Lebanon and the surrounding regions (most were located in Israel), the working hours found within the spyware’s SSH log correspond with Eastern European and Middle Eastern time zones.
“Despite unsophisticated techniques and the level of operational security being used, the attack managed to remain undetected for several years.”
More tellingly, WHOIS data uncovered two of the domains used to be registered to someone from Lebanon and other domains were registered using false data.
Perhaps foolishly, the Facebook profiles used had also liked a variety of military groups, and one called Lebanon & Israel Friendship Connection, all unlikely interests for the people these profiles supposedly belonged to and notable for once again indicating a Lebanese connection.
The report concludes that while they cannot be 100% sure, it is probable that the aforementioned Lebanese hacking group was behind the attacks.
However, the true concern regarding the attack comes in the report’s final observations. “Despite unsophisticated techniques and the level of operational security being used, the attack managed to remain undetected for several years,” it said.
By taking advantage of social media and victims’ lack of security awareness, the attackers were able to install a piece of spyware that was persistently exfiltrating private and sensitive data.
At the moment, Avast is one of the few mobile antivirus providers detecting the threat, and law enforcement agencies have been contacted to assist with mitigation.
Image courtesy of Twin Design / Shutterstock.com